To connect SharePoint to a Knowledge knowledge base, you must either provide your SharePoint credentials to NiCE Professional Services or enter them in Knowledge yourself. This page describes how to generate those credentials, also called OAuth tokens. You should treat the OAuth tokens like passwords. Be sure to store them in a secure location. If you lose them, you'll have to regenerate them.
This method is a developer effort. It requires knowledge of Python and SharePoint admin privileges.
Complete each of these tasks in the order given.
Install Python
Complete this task if you don't already have Python installed on your computer.
-
Run the installer. Select the box for Add python.exe to PATH, then click Install Now.
Register Your SharePoint Site
Register your SharePoint site with Microsoft Azure.
-
Navigate to portal.azure.com
 and sign in.
and sign in. -
Use the search bar at the top to search for App registrations and select it in the results.
-
Click New registration.
-
Enter the Name of your SharePoint site.
-
Under Supported account types, select Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant).
-
Click Register.
Copy and Store Client ID and Tenant ID
When you register your SharePoint site, Azure automatically generates the client ID and tenant ID. These are two of the credentials needed to connect SharePoint to Knowledge.
-
If you haven't already, open the site registration you created in the previous section.
-
Click Overview in the left menu.
-
Copy and paste the following credentials into a secure location:
-
Application (client) ID
-
Directory (tenant) ID
-
Add a Client Secret
Then, add a client secret for this app registration. This generates a client secret value and client secret ID, two more credentials you need to provide to Knowledge.
-
In the app registration you created, click Manage > Certificates & secrets in the left menu.
-
Click the Client secrets tab.
-
Click New client secret.
-
Enter a Description for this client secret.
-
In the Expires drop-down, select the amount of time you want to pass before the client secret expires. NiCE recommends 730 days (24 months).
-
Click Add.
-
Copy and paste the following credentials into a secure location:
-
Value
-
Secure ID
After you copy the secure ID, it is hidden.
-
Configure the Redirect URI
Next, configure the redirect URI for this app registration.
-
In the app registration you created, click Manage > Authentication in the left menu.
-
Click Add a platform.
-
In the Configure platforms form, select Web.
-
Under Redirect URIs, enter https://{aws-region}.console.aws.amazon.com/appflow/oauth. For example, if you are in the us-west-2 region, enter the following: https://us-west-2.console.aws.amazon.com/appflow/oauth
Do not select the checkboxes at the end of the form.
-
Click Configure.
Add API Permissions
Follow these steps to configure both Sites and offline_access permissions to the app registration.
Add Sites Permissions
-
In the app registration you created, click Manage > API permissions in the left menu.
-
Click Add a permission.
-
In the Request API permissions form, select Microsoft Graph.
-
Select Application permissions.
-
In the search bar that appears, enter Sites.
-
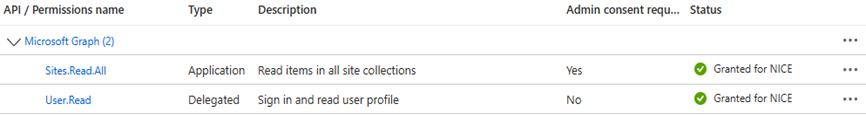
Select each permission that appears under the Sites drop-down and click Add permissions.
-
In the Configured permissions list, click Grant admin consent for NiCE.
Add offline_access Permissions
-
Click Add a permission.
-
In the Request API permissions form, select Microsoft Graph.
-
Select Delegated permissions.
-
In the search bar that appears, enter offline_access.
-
From the results, check the box next to offline_access. This permission allows the app to receive refresh tokens for long-lived access.
-
Click Add permissions.
-
In the Configured permissions list, click Grant admin consent for NiCE.
Copy and Store Site ID and Drive ID
Next, use Microsoft Graph to generate the site ID and drive ID, two more credentials you need to provide to Knowledge.
-
Navigate to developer.microsoft.com/en-us/graph/graph-explorer
 . Sign in using the same credentials you used on portal.azure.com.
. Sign in using the same credentials you used on portal.azure.com. -
In the query bar at the top, enter https://graph.microsoft.com/v1.0/sites/root and click Run query. Make sure the drop-downs to the left of the query bar are set to GET and v1.0.
-
Locate the site ID in the id attribute of the response. Copy and paste it into a secure location.
-
Enter https://graph.microsoft.com/v1.0/sites/{site-id}/drives in the query bar. Replace {site-id} with the ID you retrieved in the previous step. Click Run query.
-
Locate the drive ID in the id attribute of the response. Copy and paste it into a secure location.
Prepare OAuth Tokens
Then, prepare the OAuth tokens for use in your Python script by using the template below.
-
Copy and paste the following lines of code into a text editor:
redirect_uri = '[Enter Redirect URI]' client_id = '[Enter Client ID]' client_secret = '[Enter Client Secret]' tenant_id = '[Enter Tenant ID]' token_url = f"https://login.microsoftonline.com/[tenant_id]/oauth2/v2.0/token" -
Change the value of the redirect_uri attribute to https://{aws-region}.console.aws.amazon.com/appflow/oauth. This should match the URL you entered in the Redirect URIs field in the app registration you created. For example, in us-west-2, enter the following: https://us-west-2.console.aws.amazon.com/appflow/oauth
-
Change the value of the client_id attribute to the Application (client) ID of the app registration you created.
-
Change the value of the client_secret attribute to the client secret value of the app registration you created.
-
Change the value of the tenant_id attribute to the Directory (tenant) ID of the app registration you created.
-
Change the value of the token_url attribute. Replace [tenant_id] with your Directory (tenant) ID.
Run the Python Script
Finally, run a Python script to retrieve your SharePoint access token, refresh token, and auth code.
-
Open a text editor and start a Python file.
-
Copy and paste the lines of code from this TXT file into your Python file.
-
Replace the values of lines 5 through 9 with the OAuth tokens you prepared.
-
Open any IDE and run the Python script.
-
Copy the URL the script generates. Paste it into your browser.
-
Authorize your account. This should be the same account you used on portal.azure.com.
-
Copy the URL of the page that appears. It should begin with https://{aws-region}.console.aws.amazon.com/appflow/oauth?code=. For example, if you are in us-west-2, it would look like this: https://us-west-2.console.aws.amazon.com/appflow/oauth?code=
-
Navigate back to your IDE. Paste the URL after the prompt Enter the redirected URL:.
-
Press Enter. Your access token, refresh token, and auth code are generated in a file named sharepoint_credentials.txt. That file is automatically saved to your desktop.